Question 2: Explain the differences between followings:
i. Cache Memory and Register
ii. Ring topology and Star topology
iii. Assembly Language and High Level Language
Question 3: Explain how you will handle following problems
(i) The response time on your disk is slow.
(ii) You need to change the video mode video mode of your monitor.
(iii) You want to know the IP address of your computer system.
Question 4: Explain how you can protect your machine from computer viruses. Explain the process of removal of a computer virus from a virus infected machine.
Question 5: Explain the followings:
(i) Table in MS-word.
(ii) Mail-merge feature of MS-word
(iii) Header and Footer
(iv) Bullets and Numbering in MS-word.
Answers:
Ans. 1
An application program is any program that performs a specific function directly for the user or, in some cases, for another application program. In other words, an application program is a complete, self-contained program that performs a specific function directly for the user.
Application program is a subclass of computer software
. These programs use the services of the computer's operating system and other supporting programs. Typical examples of software applications are word processors, spreadsheets, database programs, web browsers, development tools, media players
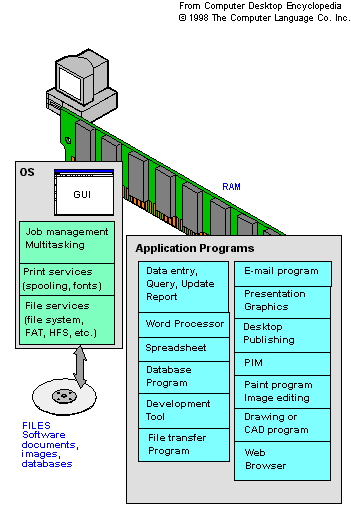
This diagram shows the typical application programs that run in a desktop computer. It also shows the major components of the operating system.
The steps for adding/removing application from a PC are as follows:
1. Click Control Panel from Start Menu
2. Click Add/Remove Programs in Control Panel
3. Then you can add/remove the required program
Ans.2 (i)
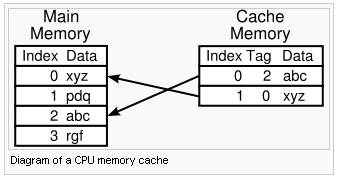
Cache Memory : Cache memory is random access memory (RAM) used by the central processing unit of a computer to reduce the average time to access memory. The cache is a smaller, faster memory which stores copies of the data from the most frequently used main memory locations. As long as most memory accesses are to cached memory locations, the average latency of memory accesses will be closer to the cache latency than to the latency of main memory.
Cache memory is extremely fast memory that is built into a computer’s central processing unit (CPU), or located next to it on a separate chip.
The advantage of cache memory is that the CPU does not have to use the motherboard’s system bus for data transfer. Whenever data must be passed through the system bus, the data transfer speed slows to the motherboard’s capability. The CPU can process data much faster by avoiding the bottleneck created by the system bus.
Cache memory is sometimes described in levels of closeness and accessibility to the microprocessor. Most computers today come with L3 cache and/or L2 cache, while older computers included only L1 cache.
A cache is made up of a pool of entries. Each entry has a datum (a nugget of data) which is a copy of the datum in some backing store. Each entry also has a tag, which specifies the identity of the datum in the backing store of which the entry is a copy.
Register: The central processing unit (CPU) contains a number of memory locations which are individually addressable and reserved for specific purpose. These memory locations are called registers. CPU instructions operate on these values directly. Registers are at the top of the memory hierarchy, and provide the fastest way for a CPU to access data.
On RISC processors, all data must be moved into a register before it can be operated. On CISC (Intel) chips, there are a few operations that can load data from RAM, process it, and save the result back out, but the fastest operations work directly with registers.
The number of registers that a CPU has and the size of each (number of bits) help determine the power and speed of a CPU. For example a 32-bit CPU is one in which each register is 32 bits wide. Therefore, each CPU instruction can manipulate 32 bits of data.
CPU registers are:
* Very fast (access times of a few nanoseconds)
* Low capacity (usually less than 200 bytes)
* Very limited expansion capabilities (a change in CPU architecture would be required)
* Expensive (more than one dollar/byte)
CPU registers may be divided into two categories:
1) User-visible registers: These registers can be accessed by programmers through machine language. These registers can be of the following categories: -
a) General Purpose – used for general purpose
b) Data – Used to hold data only
c) Address – Used to hold addresses only
d) Conditional codes – used to store flags
2) Control and status registers: These registers are used by the CU to control operations of the CPU, and by operating system programs to control program execution.
Ans.2 ii.
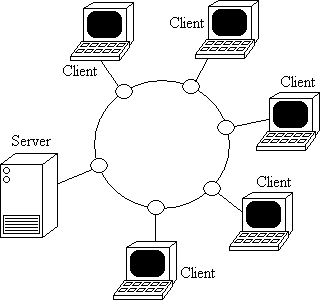
Ring topology: A network topology is a ring network in which each node connects to exactly two other nodes, forming a circular pathway for signals: a ring. Data travels from node to node, with each node handling every packet.
Because a network or ring topology provides only one pathway between any two nodes, ring networks may be disrupted by the failure of a single link. A node failure or cable break might isolate every node attached to the ring. FDDI networks overcome this vulnerability by sending data on a clockwise and a counterclockwise ring: in the event of a break data is wrapped back onto the complementary ring before it reaches the end of the cable, maintaining a path to every node along the resulting "C-Ring". 802.5 networks -- also known as IBM Token Ring networks -- avoid the weakness of a ring topology altogether: they actually use a star topology at the physical layer and a Multistation Access Unit to imitate a ring at the datalink layer.
Many ring networks add a "counter-rotating ring" to form a redundant topologies. Such "dual ring" networks include Spatial Reuse Protocol, fiber distributed data interface, and Resilient Packet Ring.
Misconceptions
* "Token Ring is an example of a ring topology." 802.5 (Token Ring) networks do not use a ring topology at layer 1. As explained above, IBM Token Ring (802.5) networks imitate a ring at layer 2 but use a physical star at layer 1.
* "Rings prevent collisions." The term "ring" only refers to the layout of the cables. It is true that there are no collisions on an IBM Token Ring, but this is because of the layer 2 Media Access Control method, not the physical topology (which again is a star, not a ring.) Token passing, not rings, prevent collisions.
* "Token passing happens on rings." Token passing is a way of managing access to the cable, implemented at the MAC sublayer of layer 2. Ring topology is the cable layout at layer one. It is possible to do token passing on a bus (802.4) a star (802.5) or a ring (FDDI). Token passing is not restricted to rings.
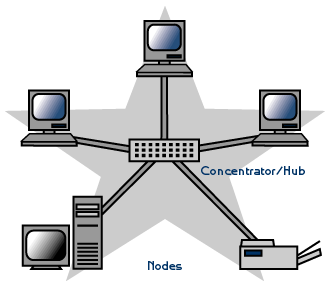
Star topology: Star topology is the most common computer network topologies.In its simplest form, a star network consists of one central switch, hub or computer, which acts as a conduit to transmit messages. Thus, the hub and leaf nodes, and the transmission lines between them, form a graph with the topology of a star. If the central node is passive, the originating node must be able to tolerate the reception of an echo of its own transmission, delayed by the two-way transmission time (i.e. to and from the central node) plus any delay generated in the central node. An active star network has an active central node that usually has the means to prevent echo-related problems.
The star topology reduces the chance of network failure by connecting all of the systems to a central node. When applied to a bus-based network, this central hub rebroadcasts all transmissions received from any peripheral node to all peripheral nodes on the network, sometimes including the originating node. All peripheral nodes may thus communicate with all others by transmitting to, and receiving from, the central node only. The failure of a transmission line linking any peripheral node to the central node will result in the isolation of that peripheral node from all others, but the rest of the systems will be unaffected.
Advantages a) Better performance
b) Isolation of devices
c) Benefits from centralization
d) Simplicity
Ans 2 (iii)
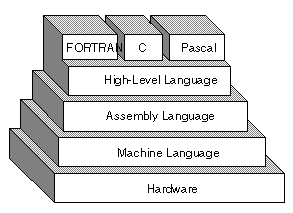
Assembly Language: An assembly language is a low-level language for programming computers. It implements a symbolic representation of the numeric machine codes and other constants needed to program a particular CPU architecture. This representation is usually defined by the hardware manufacturer, and is based on abbreviations (called mnemonics) that help the programmer remember individual instructions, registers, etc. An assembly language is thus specific to a certain physical or virtual computer architecture (as opposed to most high-level languages, which are usually portable).
Assembly languages were first developed in the 1950s, when they were referred to as second generation programming languages. They eliminated much of the error-prone and time-consuming first-generation programming needed with the earliest computers, freeing the programmer from tedium such as remembering numeric codes and calculating addresses. They were once widely used for all sorts of programming. However, by the 1980s (1990s on small computers), their use had largely been supplanted by high-level languages, in the search for improved programming productivity. Today, assembly language is used primarily for direct hardware manipulation, access to specialized processor instructions, or to address critical performance issues. Typical uses are device drivers, low-level embedded systems, and real-time systems.
High Level Language: A programming language such as C, FORTRAN, or Pascal that enables a programmer to write programs that are more or less independent of a particular type of computer. Such languages are considered high-level because they are closer to human languages and further from machine languages. In contrast, assembly languages are considered low-level because they are very close to machine languages.
The main advantage of high-level languages over low-level languages is that they are easier to read, write, and maintain. Ultimately, programs written in a high-level language must be translated into machine language by a compiler or interpreter.
The first high-level programming languages were designed in the 1950s. Now there are dozens of different languages, including Ada, Algol, BASIC, COBOL, C, C++, FORTRAN, LISP, Pascal, and Prolog.
Ans. 3 (i)
The response time on your disk is slow:
Of all of the components that make up your computer, the hard disk drive is the one most important single component that requires the most attention and maintenance.
It is in constant use and is responsible for all communication with the CPU, saving data, storing data and retrieving data like a mad thing possessed and, if it is not maintained properly it will rebel big style and you'll you'll end up with a very slow computer due entirely to a slow hard disk.
There are magnetic platters inside the hard drive and these are in an almost continous spinning motion. The heads inside the hard drive which are responsible for both reading and writing data to the disk flutter at a mind boggling speed across the platter surface.
Over time, the hard disk is subjected to a number of CPU processes that modify and add all sorts of data that is stored on the drive and this data gets amazingly fragmented.
How to fix:
Fortunately having thrown all of your data onto your hard drive in a random manner you are then able to tidy it up again with some easy to use system tools commonly known as hard disk defragmentation utilities.
Disk Defragmenter is a computer program designed to increase access speed (and sometimes increase the amount of usable space) by rearranging files stored on a disk to occupy contiguous storage locations, or defragmenting. The purpose is to optimize the time it takes to read and write files to/from the disk by minimizing head travel time and maximizing the transfer rate.
You need to change the video mode video mode of your monitor:
It sounds like the computer is set up to use a higher resolution than your monitor can produce. What you need to do is go into the boot menu by pressing and holding the F8 key just after the text of the boot process begins appearing on your screen until a list of options comes up on the screen. One of those will be to enable VGA mode. This will set Windows back to using the basic 800 x 600 resolution. Highlight that option (using the arrow keys) and then press Enter. Your screen should work just fine now.
Once into Windows, right-click on any part of your desktop where there are no icons nearby and click on Properties. A small window called "Display Properties" should appear. Click on the tab titled Settings. You will see a slider there about halfway down that is called Screen Resolution. You can move that to whatever resolution you wish as the computer should have detected what resolutions are possible with your monitor. Once you select the resolution you want, click Apply and OK.
You want to know the IP address of your computer system:
Depends on the OS:
Windows 98: Start > Run > type WINIPCFG
Windows XP: Start > Control Panel > Network Connections > Right Click > Properties
or use ip address tracker available on internet as on http://www.ip-adress.com/
Computer can be protected from virus in many ways for example:
a) By installing a good anti virus and check for regular update
b) By installing a good firewall.
c) Avoid surfing to malicious sites.
d) Avoid installing suspicious softwares
Virus can be removed from infected computer in following ways:
1. Delete Temporary Files
2. Get a good all in one Antivirus/Anti Spyware/ Anti Adware program
3. Scan whole pc including registry and all .dll files
4. Remove the suspicious file permanently or move to virus vault.
5. If needed restart the computer
Table in MS-word: It's a matrix of cells (boxes) defined by lines in which you can type words.
place your cursor where you want the table to appear and use the Table command, and Insert/Table, first choosing the number of boxes you want across and down
Mail-merge feature of MS-word:
You use mail merge when you want to create a set of documents that are essentially the same but where each document contains unique elements. For example, in a letter that announces a new product, your company logo and the text about the product will appear in each letter, and the address and greeting line will be different in each letter.
Using mail merge, you can create:
* A set of labels or envelopes The return address is the same on all the labels or envelopes, but the destination address is unique on each one.
* A set of form letters, e-mail messages, or faxes The basic content is the same in all the letters, messages, or faxes, but each contains information that is specific to the individual recipient, such as name, address, or some other piece of personal data.
* A set of numbered coupons The coupons are identical except that each contains a unique number
Creating each letter, message, fax, label, envelope, or coupon individually would take hours. That's where mail merge comes in. Using mail merge, all you have to do is create one document that contains the information that is the same in each version. Then you just add some placeholders for the information that is unique to each version. Word takes care of the rest.
Start the mail merge process
To start the mail merge process:
1. Start Word.
A blank document opens by default. Leave it open. If you close it, the next step won't work.
2. On the Tools menu, point to Letters and Mailings, and then click Mail Merge.
Note In Word 2002, on the Tools menu, point to Letters and Mailings, and then click Mail Merge Wizard.
The Mail Merge task pane opens. By using hyperlinks in the task pane, you navigate through the mail-merge process.
HEADER:
(1) In many disciplines of computer science, a header is a unit of information that precedes a data object. In a network transmission, a header is part of the data packet and contains transparent information about the file or the transmission. In file management, a header is a region at the beginning of each file where bookkeeping information is kept. The file header may contain the date the file was created, the date it was last updated, and the file's size. The header can be accessed only by the operating system or by specialized programs.
In e-mail, the first part of an e-mail message containing controlling and meta-data such as the Subject, origin and destination e-mail addresses, the path an e-mail takes, or its priority. The header will contain information about the e-mail client, and as the e-mail travels to its destination information about the path it took will be appended to the header.
(2) In word processing, one or more lines of text that appears at the top of each page of a document. Once you specify the text that should appear in the header, the word processor automatically inserts it.
Most word processors
allow you to use special symbols in the header that represent changing values. For example, you can enter a symbol for the page number, and the word processor will automatically replace the symbol with the correct number on each page. If you enter the date symbol, the word processor will insert the current date, which will change if necessary each time you print the document.
Most word processors allow you to specify different headers, for example, one for odd-numbered pages (odd headers) and another for even-numbered pages (even headers). Headers are also called running heads.
FOOTER:
One or more lines of text that appear at the bottom of every page of a document. Once you specify what text should appear in the footer, the application automatically inserts it.
Most applications allow you to use special symbols in the footer that represent changing values. For example, you can enter a symbol for the page number, and the application will replace the symbol with the correct number on each page. If you enter the date symbol, the application will insert the current date, which will change if necessary each time you print the document.
You can usually specify at least two different footers, one for odd-numbered pages (odd footer) and one for even-numbered pages (even footer).
A footer is sometimes called a running foot.
BULLETS in MS-Word:
Bullets allow you to organize text in lists. Bullets are useful for unordered lists in which each item is not significantly more important than others.
Using Bullets in Microsoft Word
Step 1. Open Microsoft Word.
Step 2. Open a new blank document using keyboard commands
* PC - Use Ctrl+N (Hold down the Ctrl key and tap the N key one time)
* Macintosh - Use Command+N (Hold down the Command key and tap the N key one time)
Step 3. Create a document which requires the use of a list. If you do not use the invitation or book report from the suggested choices above, your document must have a list of at least five things. Use a separate line for each item in your list.
Step 4. Add bullets to your list. That can be done in two ways.
1. Highlight the entire list
2. Select the bulleted list button
3. Bullets appear by each item in your list.
or
4. Place your cursor where your list will begin.
5. Select the bulleted list button
6. Type in your items one at a time.
7. Press Return/Enter at the end of each item.
8. Bullets appear at the beginning of each item you type.
Step 7. After completing your list and pressing Return/Enter another bullet will appear. To remove that bullet, deselect the bullet button in the formatting toolbar.
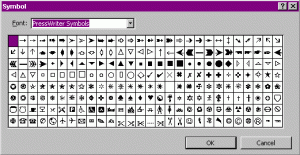
Step 8. You may change the style of your bullets. Highlight the five bulleted points. Go to the Format menu, select Bullets and Numbering. From the display on the Bulleted tab, select one of the styles of bullets. After choosing one, you can see a much larger selection of bullets by clicking on the Customize tab. From the Customize bulleted list dialog box you may change the font and/or the bullet.
As an example, the sample dialog box above shows bullets available in only one font. Every font on your computer has some bullets you might use. Some of the fonts are nothing but images and icons which could be used as bullets.
Numbering in MS-word:
Numbering allows you to organize text in lists. Numbering is useful for lists in which each item is part of a sequence of steps and ought to be followed in that order. By using list levels, you can organize numbering into categories. List levels can express categories through any combination of indentation, font size, and numbering styles or list styles